Phishing Emails Are Getting More Creative | Stewart Title Blog
Cybercriminals follow our every move. With every countermeasure we put in place, they create a workaround shortly thereafter. This week I picked an interesting email to demo.
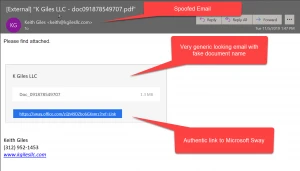
At first glance, nothing is out of the ordinary in this email. It meets all the qualifications of typical spam or phishing email: unrecognized sender, no recipient in the "to:" field, no greeting and very suspicious content. What’s interesting here is the link. The link shows no red flags. It points to the Microsoft product named Sway. Sway is included with some versions of Office 365 and is essentially Word on steroids. It’s a rich content-creation tool used to design and publish electronic newsletters and presentations. In order to create the content, one needs to have an Office 365 account. However, no account or authentication is needed to post the content results to a public platform. Few other Microsoft products have similar capabilities, but they can all be abused in the same way.
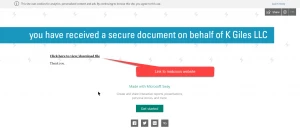
In this example, the Sway document has another link that points to a malicious website. Why would a criminal go to this extent, you ask? The original email is completely benign from the view of any security filtering technology. It has no attachments and contains a legitimate link.
They know many of their emails are not making it through because of the different layers of security we put in front of you. Making an email benign makes our first line of defense completely useless. The sender, K Giles LLC, is a paying Office 365 user who is potentially a bad actor or a person whose credentials were stolen.
Fortunately, the employee was vigilant and reported the email to the security team. Keep up the excellent work and always remember to think before you click.
