The Danger Lurking Inside HTML Files and Bit.ly Links | Stewart Title Blog
One email, four different attack vectors. I’ve covered the different elements in the past, but it was interesting to see multiple techniques combined. The email (1) immediately meets the definition of spam/phish: obscure sender, no recipient, no greeting and a real estate-relevant attachment name. The first red flag is the attachment extension. Html is a relatively uncommon extension type for an attachment and will be open in your default browser. It's not a new trick, but it’s still used to fool email security filtering systems.
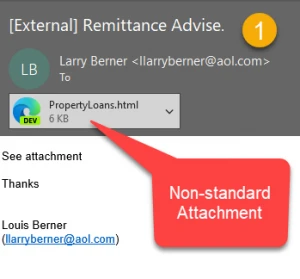
The attachment (2) looks like an email message, but it's not. If you’re not careful, you may think it's legitimate, as we are all now accustomed to secure email communications that use a web browser. The first two links point to the same phishing site posing as an MLS listing. Note that it even has a friendly MLS disclaimer. We’ve talked about the abuse of the unsubscribe link before, and here’s a perfect example. On this bogus page, the link points to yet another phishing website. As part of the master plan, the thief uses a URL-shortening Bitly link.

What did we learn today?
- File attachments with .html extension are rare and should always be evaluated with caution.
- Footers and headers that include legitimate technologies or legitimate-sounding content create an artificial authenticity or relevancy.
- Unsubscribe buttons and links are now abused by cybercriminals to phish out credentials. Remember, a legitimate unsubscribe website will never ask for any credentials. The “attack environment” has changed over the last few years, and many across the security community suggest deleting emails that ask you to unsubscribe instead of clicking the link.
- URL-shortening tools like Bitly are often used in criminal activities, and you never know where you’re going until you click on the URL. Always proceed with caution.
And don’t forget to think before you click.
