Recognize Phishing Emails Before You're Caught | Stewart Title Blog
Phishing emails meant to steal email credentials continues to get through our mailboxes. In our industry, anything to do with closing files gets the easy catch - familiar words used in subject lines, body copy, and attachments. Hackers know and use our timing to their advantage; they know the ends of the week and month are the busiest time for us. That’s when we’re more stressed and most vulnerable. Remember:
- Examine the initial email for any red flags. Ask yourself:
- Do I know the sender?
- Is it addressed to me?
- Is it relevant (my file, my customer, my property)?
- Am I expecting it?
- Does it have proper language, punctuations, formatting, signature?
- If you can check off those questions, which is rare, click on the link, but ask:
- Is the web page asking me for corporate or other credentials to get what I need?
- How does the sender know my address?
- Would it be smarter to just run away?
- If you’re in doubt or uncomfortable with anything about the email, always pick up the phone and call IT before clicking.
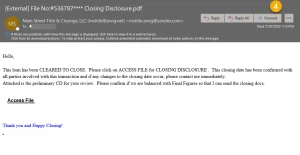
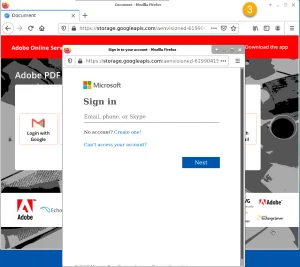
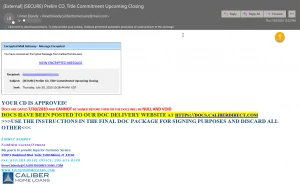
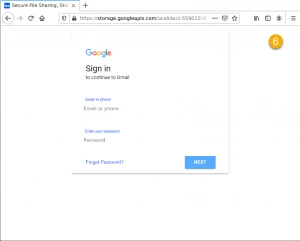
Examples of how these emails may look
In examples 1 and 4, if you click on the link, you’ll land on the website with every possible login option, as examples 2 and 5 show. That’s a pretty sneaky way to try and steal information. In examples 3 and 6, once you enter your password, the hacker has access to your email account. If you went all the way through, now would be a good time to reset your password.

Example 1
Example 2
Example 3

Example 4
Example 5
Example 6
